[ad_1]
Log4j was the bucket of cold water that woke up most builders to their application source chain security dilemma.
We have expended many years in program creating factors and obsessing above our manufacturing atmosphere. But we’re creating on unpatched Jenkins boxes sitting less than someone’s desk. We invest all this time preserving our runtimes, then deploy to them utilizing newbie tooling.
Our create environments aren’t virtually as protected as our generation environments.
That’s what led to a whole ton of higher-profile attacks in the very last 12 months, from SolarWinds, to the Codecov assault, to the Travis CI strategies leak. We’ve gotten so great at preserving our infrastructure that attackers looked for an a lot easier way in, and located it in the doorways we have remaining open in the offer chain.
Just cannot get in by way of the perimeter security? Just obtain an open resource dependency, or a library, and get in that way. Then pivot to all of the customers. This is the modern application source chain hack.
We will need roots of believe in for computer software
We have roots of belief for persons today. We have two-factor authentication, we have identification units. These are matters to vouch for a person’s identity. And hardware has the exact same issue. We have encryption keys. We have components we can rely on has not been tampered with when it boots up.
Even as world wide web customers we have roots of have faith in. We have URIs, URNs, and URLs—effectively the namespaces on the net that connect the identities, names, and spots of web pages we are browsing. SSL certificates inform our browsers that web pages are secure. DNS firewalls sit in between the user’s recursive resolvers to make sure our cache isn’t remaining loaded with bad requests. All of this is taking place powering the scenes, and has been extremely effective in supporting billions of world-wide-web people for many years.
But we don’t have this for application artifacts currently.
Developers rely on far too substantially implicitly
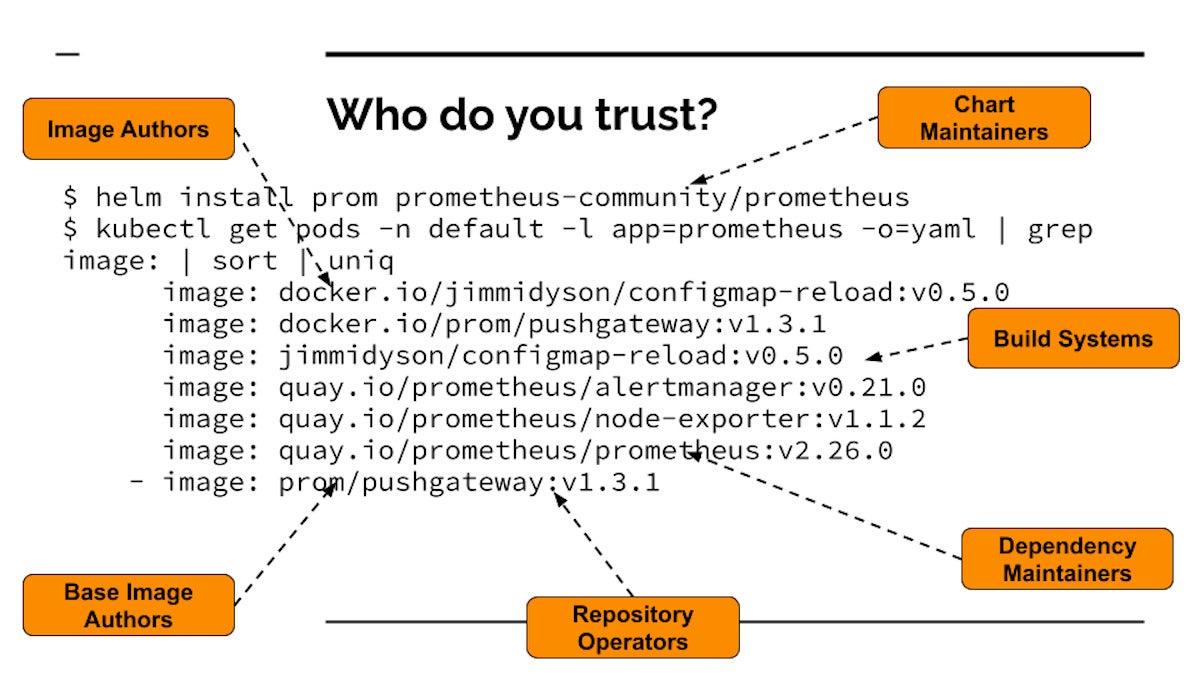
Take an party as commonplace as installing Prometheus (a well-known open up supply observability challenge) from the Cloud Native Computing Basis (CNCF) artifact hub. If you do your Helm put in and then look at all the illustrations or photos that get pulled and get started running your cluster, you see lots of container pictures that finish up working from a straightforward installation. Developers are entrusting a whole bunch of points to a total bunch of diverse people today and systems. Every one one of these could be tampered with or attacked, or could be malicious.
 Dan Lorenc
Dan LorencThis is the opposite of Zero Trust—we’re trusting dozens of units that we really don’t know anything about. We really don’t know the authors, we do not know if the code is malicious, and simply because each impression has its have artifacts, the entire supply chain is recursive. So we’re not only trusting the artifacts, but also the people who reliable the dependencies of these artifacts.
We’re also trusting the persons who operate the repositories. So if the repository operators get compromised, now the compromisers are aspect of your rely on circle. Anyone managing just one of these repositories could improve a little something and assault you.
Then there’s the establish devices. Build units can get attacked and insert destructive code. That is particularly what transpired with SolarWinds. Even if you know and trust the operators of the visuals, and the people operating the programs that host the photographs, if these are crafted insecurely, then some malware can get inserted. And all over again it is recursive all the way down. The dependency maintainers, the make techniques they use, the artifact managers that they are hosted on—they’re all undermined.
So when developers put in application offers, there are a great deal of items they are trusting implicitly, regardless of whether they mean to have confidence in them or not.
Computer software source chain stability gotchas
The worst system you can have in program provide chain security is to do nothing at all, which is what a lot of builders are performing nowadays. They are letting anything at all to operate on generation environments. If you have no protection all-around what artifacts can operate, then you have no notion exactly where they came from. This is the worst of the worst. This is not shelling out interest at all.
Allow for-listing precise tags is the subsequent amount up. If you go by way of some of the tutorials all-around finest practices with Kubernetes, this is pretty effortless to established up. If you force all your visuals to a solitary area, you can at minimum restrict points to that place. Which is way much better than accomplishing nothing at all, but it is however not good, simply because then something that gets pushed there is now inside your believe in circle, within that barbed wire fence, and that is not really Zero Have faith in. Let-listing certain repositories has all the exact restrictions of allow-listing certain tags.
Even the signing schemas in supply chain protection are papering about the similar challenge. Something that will get signed now will get to run, irrespective of wherever it came from, which leads to tons of attacks tied to tricking an individual to indication the wrong point, or becoming unable to revoke a certificate.
Time to commence inquiring the ideal inquiries
Let’s say you are walking down the sidewalk outside the house of your workplace, and you uncover a USB thumb push sitting down on the ground. I hope absolutely everyone knows that you need to definitely not consider that push inside of your office and plug it into your workstation. Absolutely everyone in program should (rightly) be screaming, “No!” Genuine attacks have transpired this way, and stability orgs throughout the earth hammer this warning into all personnel as portion of training.
But for some reason, we don’t even pause to feel twice ahead of jogging docker pull or npm set up, even even though these are arguably even worse than plugging in a random USB adhere. The two circumstances entail taking code from somebody you do not trust and running it, but the Docker container or NPM package deal will eventually make it all the way into your manufacturing surroundings!
The essence of this provide chain stability evolution is that as an marketplace we’re relocating absent from trusting in which the software package artifacts come from, and paying a lot a lot more time figuring out roots of have faith in for what the artifact is.
Who posted this binary? How was it constructed? What edition of the device was used? What supply was it designed from? Who signed off on this code? Was nearly anything tampered with? These are the ideal questions to be asking.
Subsequent 7 days, we’ll glance at the rapid-evolving open up source landscape that is forming a new security stack for supply chain security, and unpack vital concepts developers will need to understand—from roots of trust, to provenance, to TPM (Trustworthy Platform Module) attestation.
Dan Lorenc is CEO and co-founder of Chainguard. Beforehand he was workers program engineer and lead for Google’s Open up Source Security Staff (GOSST). He has launched initiatives like Minikube, Skaffold, TektonCD, and Sigstore.
—
New Tech Discussion board supplies a venue to investigate and examine rising organization engineering in unparalleled depth and breadth. The variety is subjective, dependent on our pick of the technologies we think to be vital and of finest curiosity to InfoWorld visitors. InfoWorld does not accept advertising collateral for publication and reserves the suitable to edit all contributed content material. Mail all inquiries to [email protected].
Copyright © 2022 IDG Communications, Inc.
[ad_2]
Resource hyperlink
